
Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.
86-0769-39020536
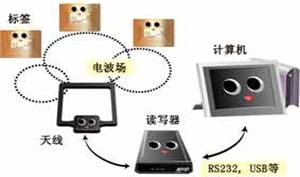 Radio Frequency Identification (RFID, Radio Frequency Identification) technology is the application and development of automatic identification technology in radio technology. The basic principle is to use radio frequency mode to conduct non-contact two-way communication in order to achieve the purpose of identification and data exchange. Therefore, it can achieve multi-target recognition, moving target recognition and remote real-time monitoring and management. The communication distance can range from a few centimeters to several tens of meters. Its main advantages are its strong adaptability to the environment, its ability to work around the clock, its non-contact automatic identification, tracking and management, and its ability to penetrate non-metallic objects for identification and anti-jamming capability. Strong.
Radio Frequency Identification (RFID, Radio Frequency Identification) technology is the application and development of automatic identification technology in radio technology. The basic principle is to use radio frequency mode to conduct non-contact two-way communication in order to achieve the purpose of identification and data exchange. Therefore, it can achieve multi-target recognition, moving target recognition and remote real-time monitoring and management. The communication distance can range from a few centimeters to several tens of meters. Its main advantages are its strong adaptability to the environment, its ability to work around the clock, its non-contact automatic identification, tracking and management, and its ability to penetrate non-metallic objects for identification and anti-jamming capability. Strong. March 08, 2024
November 29, 2023
Email ke pemasok ini
March 08, 2024
November 29, 2023

Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.

Fill in more information so that we can get in touch with you faster
Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.